Problem Statement
Nowadays DevOps guys use terraform quite a lot for creating resources in AWS, GCP, or AZURE cloud platforms. But while maintaining terraform versioning they use various Version Control Systems like git, bitbucket and while pushing the code they do commit the passwords in plaintext which are required to create resources like AWS RDS, documentDB, etc.
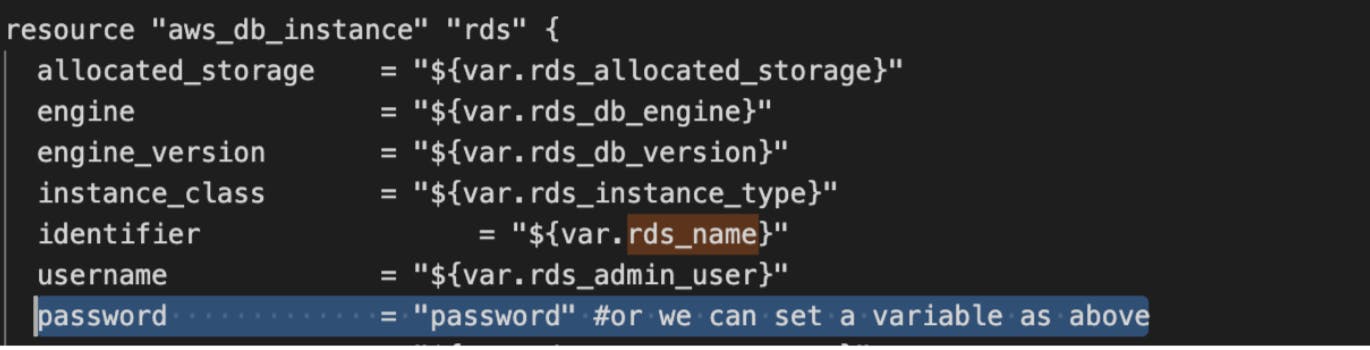
So to protect our sensitive information like plaintext passwords which in our case is “password” we can do a few changes in our terraform code to get rid of this problem without using any 3rd party tools.
Resolution
Here Let’s take an example of creating AWS RDS as a resource from terraform. Create a directory “sensitive-information” to store your password file separately.
mkdir sensitive-information
cd sensitive-information
Create a JSON file to store your password
echo “{ \”password\”: \”ourpassword\” }” >> sensitive-information/rds_pass.json
Not we will use the data module of terraform to read the AWS RDS password from the JSON file.
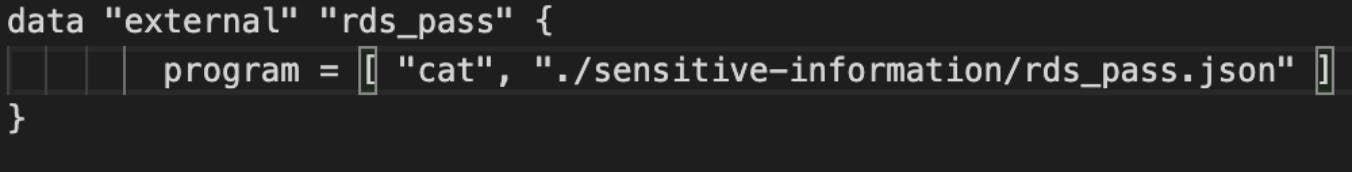
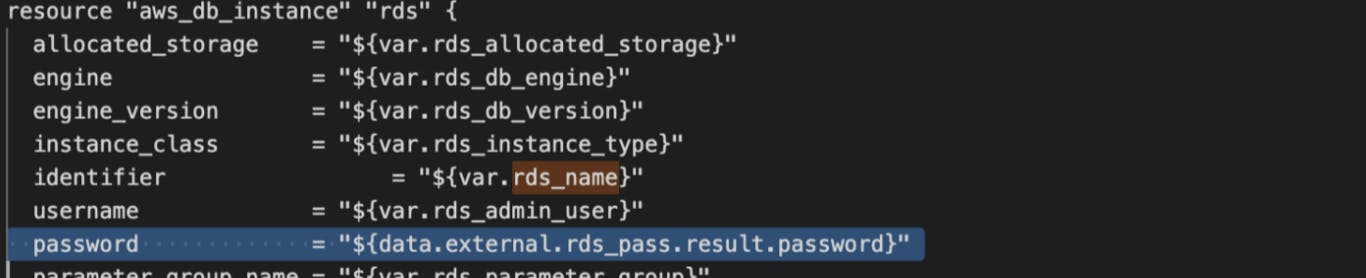
Now we are almost done just passing this data as a password in the aws_db_instance resource.
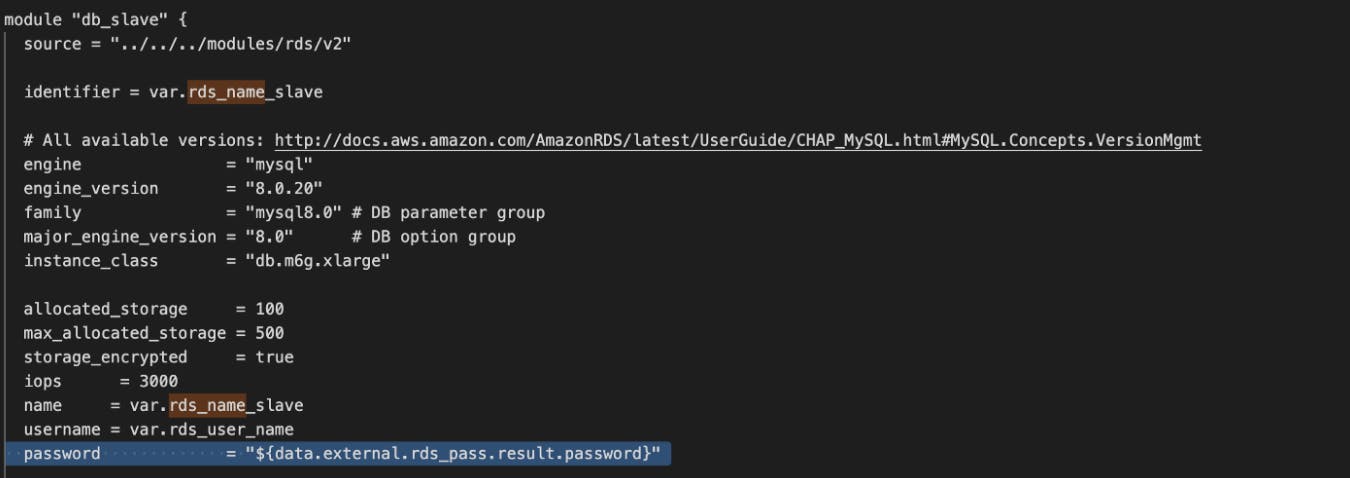
or if we have set up the module-wise architecture of terraform we can also add this to the main directory from where you are calling this aws_db_instance resource a module.
Now we are good to go just encrypt the rds_pass.json and you will get rds_pass.json.gpg
gpg -o sensitive-information/rds_pass.json.gpg \ — batch \ — symmetric \ — openpgp \ — cipher-algo AES256 \ — s2k-cipher-algo AES256 \ — s2k-digest-algo SHA512 \ — s2k-mode 3 \ — s2k-count 65011712 \ — armor \ — emit-version \ sensitive-information/rds_pass.json
Now you can add rds_pass.json in your .gitignore and push the changes in git only rds_pass.json.gpg file will be committed later you can use that file to decrypt your passwords.
Note
I hope this article will help you to protect your passwords from exposure, these issues are being faced by the company who are in their beginning phase to starting with terraform and got into securities issues of exposing passwords or any other sensitive information.

